Gain Enterprise-Level Threat Detection and Autonomous Response Power
C‑Prot EDR (Endpoint Detection and Response) detects and blocks modern attacks in real time through behavioral analytics, AI-powered detection engines, and automated response capabilities. With deep telemetry visibility, attack correlation, and Storyline-based analysis, it enables security teams to respond to incidents quickly and effectively.
Machine-Speed Threats
Attackers can now infiltrate systems within milliseconds using automation and artificial intelligence. While traditional solutions fall short against this speed, C‑Prot EDR’s behavioral analytics and autonomous protection stop threats in real time.
Expanded & Converged Attack Surfaces
Endpoint, identity, and network surfaces are becoming increasingly interconnected every day. This convergence reduces visibility and makes it easier for attackers to move unnoticed. C‑Prot EDR (Endpoint Detection and Response) provides unified visibility across every layer — from endpoints to identity activities — with a single agent.
Overloaded SOC Teams
Today’s SOC teams are struggling with increasing complexity and shrinking resources. This pressure makes rapid decision-making and effective incident management more difficult. C‑Prot Deep Black AI reduces analyst workload dramatically with natural-language queries, automated summarization, correlation, and intelligent recommendations.
Stop Advanced Threats with Autonomous Protection and Deep Visibility
Machine-speed prevention: C‑Prot’s behavioral and static AI engines detect suspicious activity before it executes, blocking modern malware in real time.
Instant ransomware detection: Behavioral analytics identify abnormal encryption patterns and lateral movement instantly; C‑Prot EDR (Endpoint Detection and Response) blocks file encryption attempts, phishing activity, and command-and-control operations.
Holistic visibility through unified telemetry: It consolidates all endpoint telemetry—from system events to identity-based attacks—into a single security context. Process, file, memory, registry, and identity activities are displayed within the same visibility layer, enabling analysts to identify critical threats at a glance.
Multi-platform protection: C‑Prot delivers zero-day-ready protection on iOS and Android devices against phishing, malware, privilege escalation, and MITM attacks.
Resolve Incidents Faster with AI-Driven Response
Autonomous and one-click remediation: C‑Prot EDR (Endpoint Detection and Response) automatically responds to detected threats, performing process kills, network isolation, rollback, and policy enforcement within seconds.
Visualize the entire attack chain with Storyline: C‑Prot Storyline technology automatically transforms endpoint, identity, and network telemetry into a contextual attack chain. Analysts can track how a threat originated and how it progresses within the environment through a single graphical timeline.
Contextual analysis and prioritization: Alerts are automatically correlated across process, file, identity, and network activities and ranked by severity. Critical threats are highlighted, enabling SOC teams to instantly determine which incidents require immediate attention.
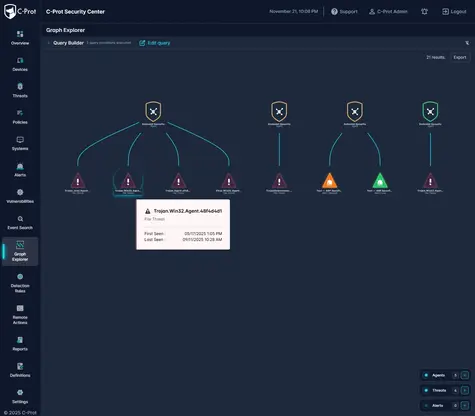
Optimize Security with a Unified, Low-Impact C‑Prot Agent
Single agent, simplified architecture: C‑Prot EDR consolidates behavioral analytics and identity-based protection into a single intelligent C‑Prot Agent. It eliminates performance issues caused by multiple agents, simplifies endpoint management, and minimizes operational complexity.
High performance across platforms: The C‑Prot Agent is optimized to deliver the same level of security and telemetry depth across Windows, macOS, Linux, and mobile operating systems. It provides consistent visibility and equal protection on every platform.
Lightweight architecture, maximum efficiency: Its design keeps CPU and memory usage low while analyzing process, file, network, and identity activities within milliseconds. It enhances endpoint visibility without compromising performance, ensuring uninterrupted device protection.
Empower Security Teams with Autonomous AI Intelligence
Natural language threat hunting: With Deep Black AI, analysts can access all telemetry — including process data, logs, identity events, and network activity — using natural language. It accelerates threat hunting without the need to write complex queries and makes critical insights visible within seconds.
Automated summaries and guided analysis: Deep Black AI automatically summarizes alerts, highlights critical findings, and recommends which component should be examined next. This creates a contextual investigation flow and significantly increases the speed of analyst decision-making.
Security-focused AI models that reduce error rates: C‑Prot’s security-focused AI models are built with accuracy, reliability, and enterprise audit requirements in mind. They minimize the risk of misleading or noisy results, enabling analysts to make faster and more accurate decisions.
 Deep Attack Analysis
Deep Attack Analysis